Neutralize threats before they hit.
Identify and mitigate cyber risks with precision. Invest in solutions that drive measurable return on security investment and power your business forward.
Corax 360° Is For Everyone
From executives to IT teams, Corax 360° provides a comprehensive solution for all stakeholders in managing cyber risks and securing your organization.
CEO
Corax 360° For CEOs
Corax 360° empowers you to lead with confidence by providing a comprehensive, data-driven approach to cyber risk management. Ensure your organization is protected from evolving threats, streamline compliance, and safeguard your bottom line—all while maximizing the return on your security investments. With Corax 360°, you can focus on growth, knowing your cyber resilience is in expert hands.
Compliance Officer
Corax 360° For CEOs
Corax 360° empowers you to lead with confidence by providing a comprehensive, data-driven approach to cyber risk management. Ensure your organization is protected from evolving threats, streamline compliance, and safeguard your bottom line—all while maximizing the return on your security investments. With Corax 360°, you can focus on growth, knowing your cyber resilience is in expert hands.
Risk Manager
Corax 360° For CEOs
Corax 360° empowers you to lead with confidence by providing a comprehensive, data-driven approach to cyber risk management. Ensure your organization is protected from evolving threats, streamline compliance, and safeguard your bottom line—all while maximizing the return on your security investments. With Corax 360°, you can focus on growth, knowing your cyber resilience is in expert hands.
CFO & Exposure Manager
Corax 360° For CEOs
Corax 360° empowers you to lead with confidence by providing a comprehensive, data-driven approach to cyber risk management. Ensure your organization is protected from evolving threats, streamline compliance, and safeguard your bottom line—all while maximizing the return on your security investments. With Corax 360°, you can focus on growth, knowing your cyber resilience is in expert hands.
IT Management
Corax 360° For CEOs
Corax 360° empowers you to lead with confidence by providing a comprehensive, data-driven approach to cyber risk management. Ensure your organization is protected from evolving threats, streamline compliance, and safeguard your bottom line—all while maximizing the return on your security investments. With Corax 360°, you can focus on growth, knowing your cyber resilience is in expert hands.
Got Questions? Corax 360° Has Answers
Cybersecurity can be complex. We’re here to make it clear. Here are the questions Corax 360° helps you answer to safeguard your organization.
Corax360™ Cyber Solutions
Enterprise-level cyber risk optimization platform.
Governance & Compliance
Ensure regulatory compliance and reduce risk with a strong governance framework.
Business Continuity Plan
Prepare for disruptions with a plan that keeps your business running smoothly.
Our Key Strengths: Securing Your Business, Simply and Effectively
Advanced Cyber Tech Solutions Designed to Tackle Real-World Challenges and Drive Measurable Results
Elite Cybersecurity Expertise at an Affordable Cost
Access top cybersecurity skills and solutions without the high overhead, making advanced protection attainable for all.
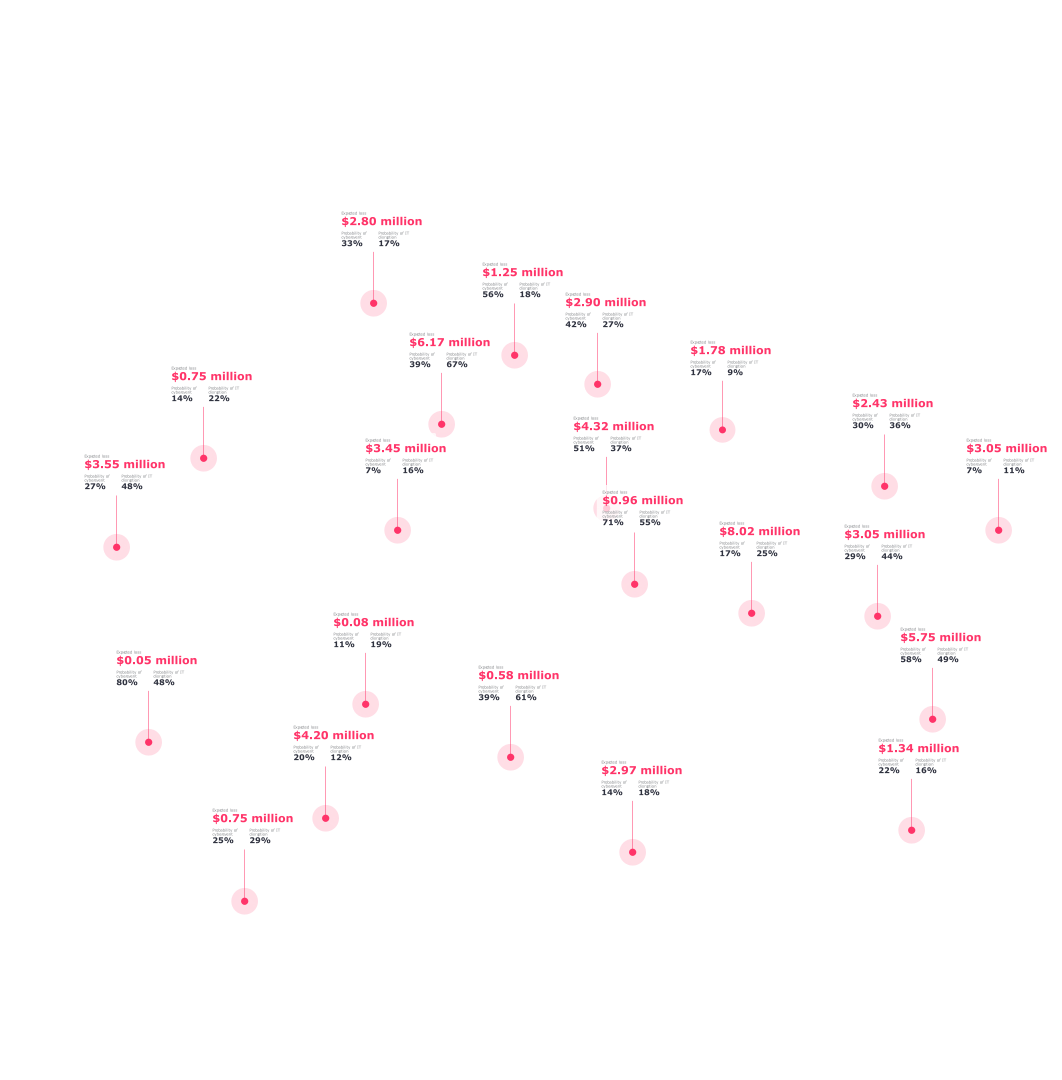
Global Cyber Exposure Modeling and Analytics
Leverage data-driven insights on the cyber exposure of millions of interconnected companies worldwide to understand risk on a global scale.
Trusted by the Insurance Industry and Beyond
Developed in collaboration with industry leaders, Corax 360° empowers not only insurers but businesses across sectors to tackle diverse challenges with precision.
Companies modelled
Companies hacked daily
Frequently Asked Questions
We’re constantly updating our cyber risk FAQs. If you have a question you’d like answered, drop us a line at [email protected].
S.O.S. Cyber Attack
US - S.O.S. Direct Hotline
UK - S.O.S. Direct Hotline
UK - S.O.S. Direct Hotline