Helping Insurers Reduce Exposure to the Cyber Quake
Last week, Corax’s Head of Insurance Innovation and Strategy, Marcus Breese and our CTO Tom Beale led our webinar, “What can WannaCry and Petya tell insurers about systemic potential of malware?”
This took place against the backdrop of the WannaCry and Petya outbreaks, the Prudential Regulation Authority (PRA) telling insurers to stress test cyber exposure, and Lloyds’ releasing its 2017 Emerging Risks Report, ‘Counting the cost Cyber exposure decoded,’ which highlighted the complexities involved in aggregating cyber related-catastrophes. At Corax we’ve always referred to the possibility of this type of significantly disruptive event as a ‘cyber quake’.
In the webinar, Marcus and Tom highlighted three actionable points to help insurers underwriting cyber exposures.
Firstly, whilst it’s important to determine if an insured has a patching policy, more insight can be gained by establishing how patching is prioritized. Patching is a complex issue. The complexity is driven by the the sheer breadth of vendors, the number of products they supply, and the ubiquitous nature of many of those products.
Total vulnerabilities in 2016, by vendor, larger font indicating more vulnerabilities (source: nvd.nist.gov):
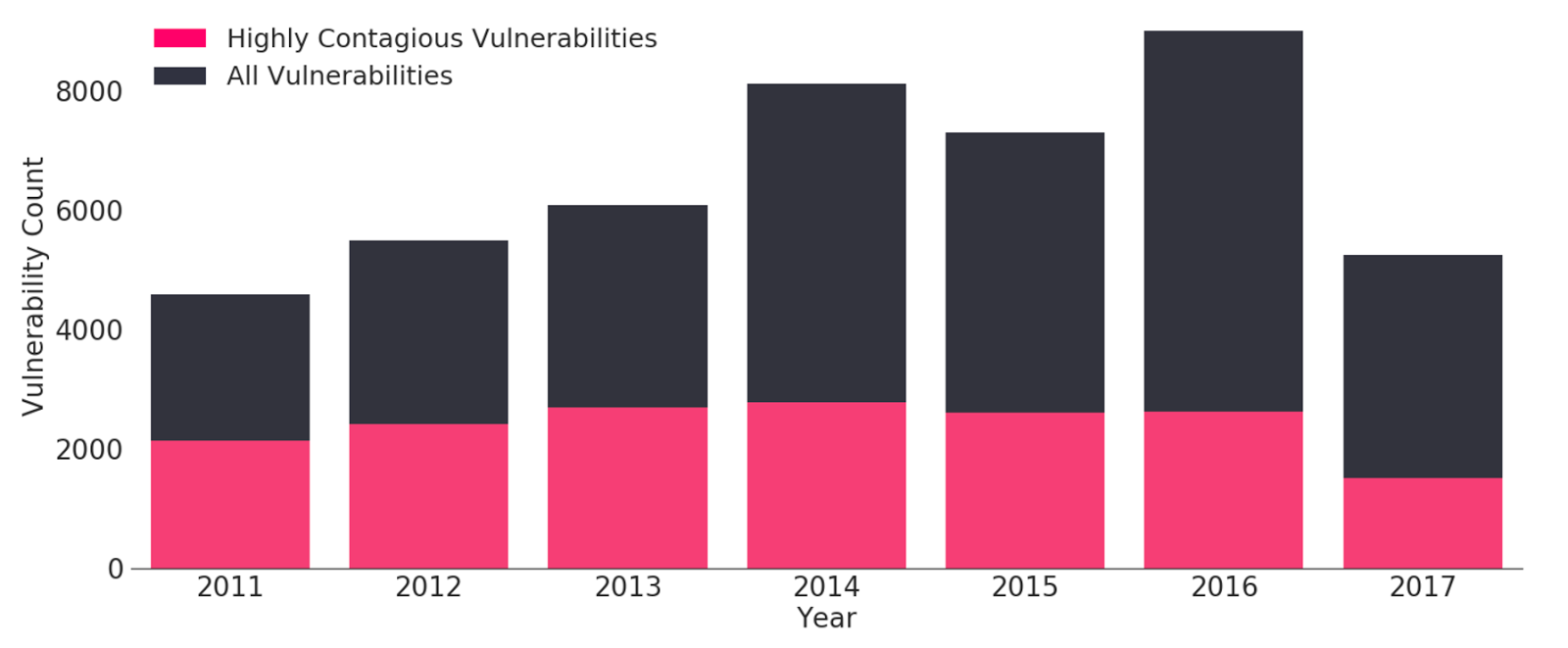
Secondly, it’s important to identify whether ‘highly contagious’ types of vulnerability remain unpatched by an insured. Highly contagious vulnerabilities are ones sharing very similar characteristics, meaning they can be exploited by the same types of malware. These present the most sideways exposure from an insurance perspective.
Total vulnerabilities subsetted with vulnerabilities that have similar ‘highly contagious’ characteristics to those exploited in WannaCry, Petya & NotPetya (Source: nvd.nist.gov):
Thirdly, policy language should change. The ‘recipe’ that makes up malware can and does change regularly. A change to an exploit (think of the horse in the battle for Troy) or to the payload (the soldiers inside the horse) are enough to create a different type of malware that will take advantage of the same vulnerability, if that vulnerability isn’t patched.
This dynamic landscape creates a challenge for insurance policy language, specifically for the way in which policies aggregate events. Petya, WannaCry and NotPetya were related by the vulnerability they exploited, the exploit through which they were deployed, and the code they had in common within the malware.
Within the insurance industry, it is the language within a policy that will dictate the extent to which ‘malware’ events are distinct or separate, specifically the breadth or otherwise of the ‘series’ or ‘aggregation’ clause.
Identifying cyber exposure, quantifying that exposure, and modelling the impact of events is a challenge for insurers. Corax can help with that challenge. However, establishing the impact on insured portfolios with accuracy is difficult where multiple definitions of the event itself exist. Consider for example the wide variety of wordings over which insurers of excess layers typically participate.
How should policy language change? Our recommendation would be to design language that is triggered by, and aggregates around vulnerabilities, rather than by malware, exploits, situations or events.
Contact us here if you’d like to discuss this, and click here to download the webinar recording.